Видео с ютуба Tunneling Metasploit

Mastering Network Pivoting in AttackDefenseLab: Advanced Techniques with Metasploit & Proxychains

Metorpreter - Metasploit's Meterpreter over TOR

HTTP tunneling with Tunna - metasploit module example run

Pivoting with Metasploit I

Metasploit Hacking Demo (includes password cracking)

Tunneling Through Protected Networks | Master Network Pivoting

Sending Metasploit through a SOCKS Proxy Pivot

Как перемещаться по сети с помощью Chisel

Reverse Shell with Meterpreter & Metasploit - Kali Linux Tutorial

ssh tunnel pivot with metasploit demo: pt1 conop & tomcat compromise
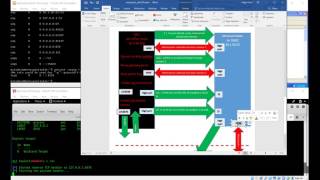
ssh tunnel pivot with metasploit: pt4 pivot and test

ssh tunnel pivot with Metasploit: pt3 set GatewayPorts and init L and R tunnels

how to get remote access to your hacking targets // reverse shells with netcat (Windows and Linux!!)

ssh tunnel pivot with metasploit: pt2 privesc & key drop

The Ultimate Metasploit Tutorial!

Metasploit For Beginners - How To Scan And Pwn A Computer | Learn From A Pro Hacker

Metasploit Full Course | Learn Ethical Hacking, Exploits, Payloads & Post-Exploitation

Don't get caught! Hide Yourself w/ Proxychains and TOR

Basic Pivoting Techniques: SSH Dynamic Port Forwarding + Metasploit over SSH